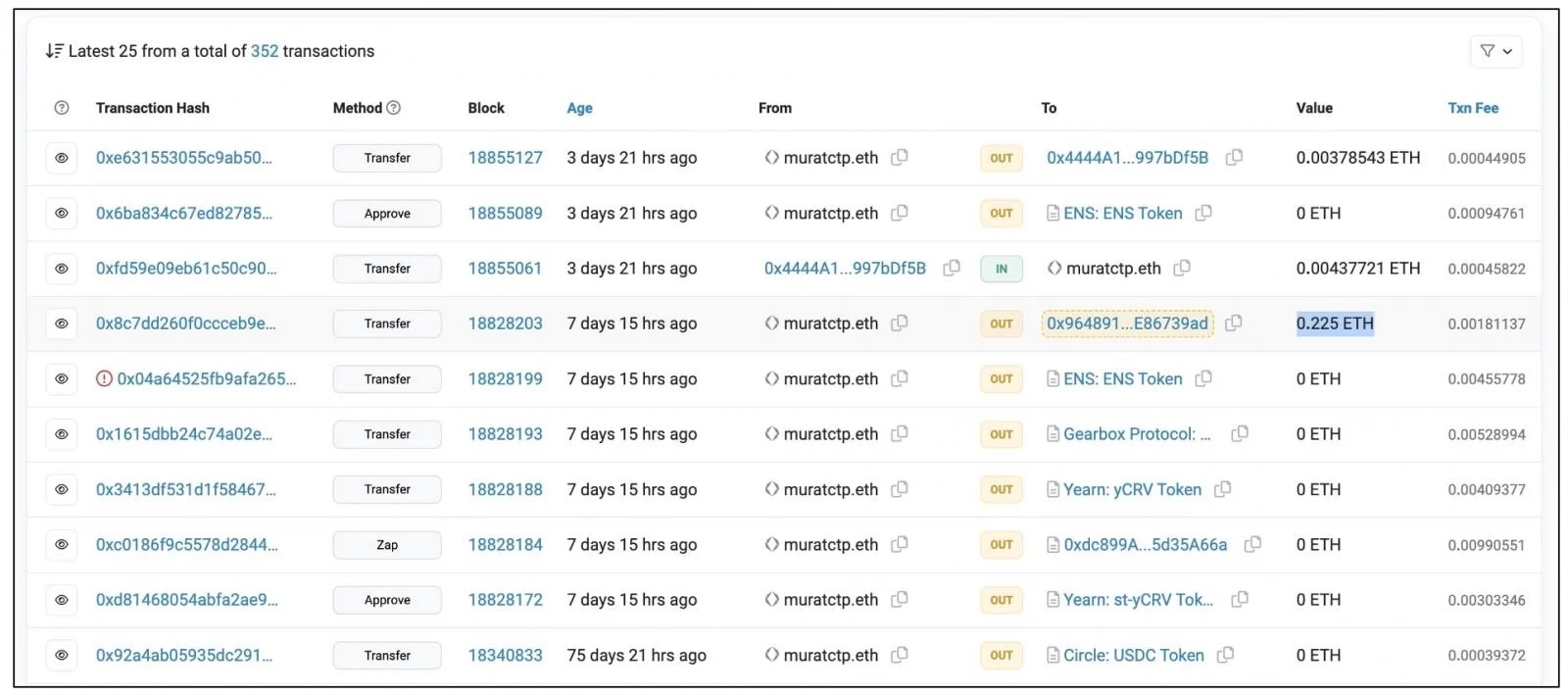
In a recent incident, a blockchain developer, Murat Çeliktepe, shared a distressing experience over the holidays after being approached on LinkedIn for what appeared to be a legitimate web development job. The “recruiter” presented an Upwork job posting, seemingly offering a genuine opportunity, and requested Çeliktepe to download npm packages from GitHub as part of the job interview. However, hours later, the developer discovered his MetaMask wallet had been emptied, with over $500 siphoned off.
In a recent incident, a blockchain developer, Murat Çeliktepe, shared a distressing experience over the holidays after being approached on LinkedIn for what appeared to be a legitimate web development job. The “recruiter” presented an Upwork job posting, seemingly offering a genuine opportunity, and requested Çeliktepe to download npm packages from GitHub as part of the job interview. However, hours later, the developer discovered his MetaMask wallet had been emptied, with over $500 siphoned off.
LinkedIn Encounter Turns Costly
Çeliktepe, based in Antalya, detailed how the LinkedIn recruiter lured him with an Upwork job posting, asking him to fix bugs and enhance website responsiveness. Despite the seemingly authentic nature of the job, the developer’s MetaMask wallet fell victim to a sophisticated attack after downloading npm packages for the “tech interview.”
Challenges in Identifying the Attack Vector
As Çeliktepe shared his ordeal on social media, he sought assistance from the community to understand the mechanics of the attack. Despite examining the code in the GitHub repositories, he remains uncertain about how his MetaMask wallet was breached. Concerningly, even without keeping the MetaMask Secret Recovery Phrase on his computer, the attack resulted in a drained Ethereum balance.
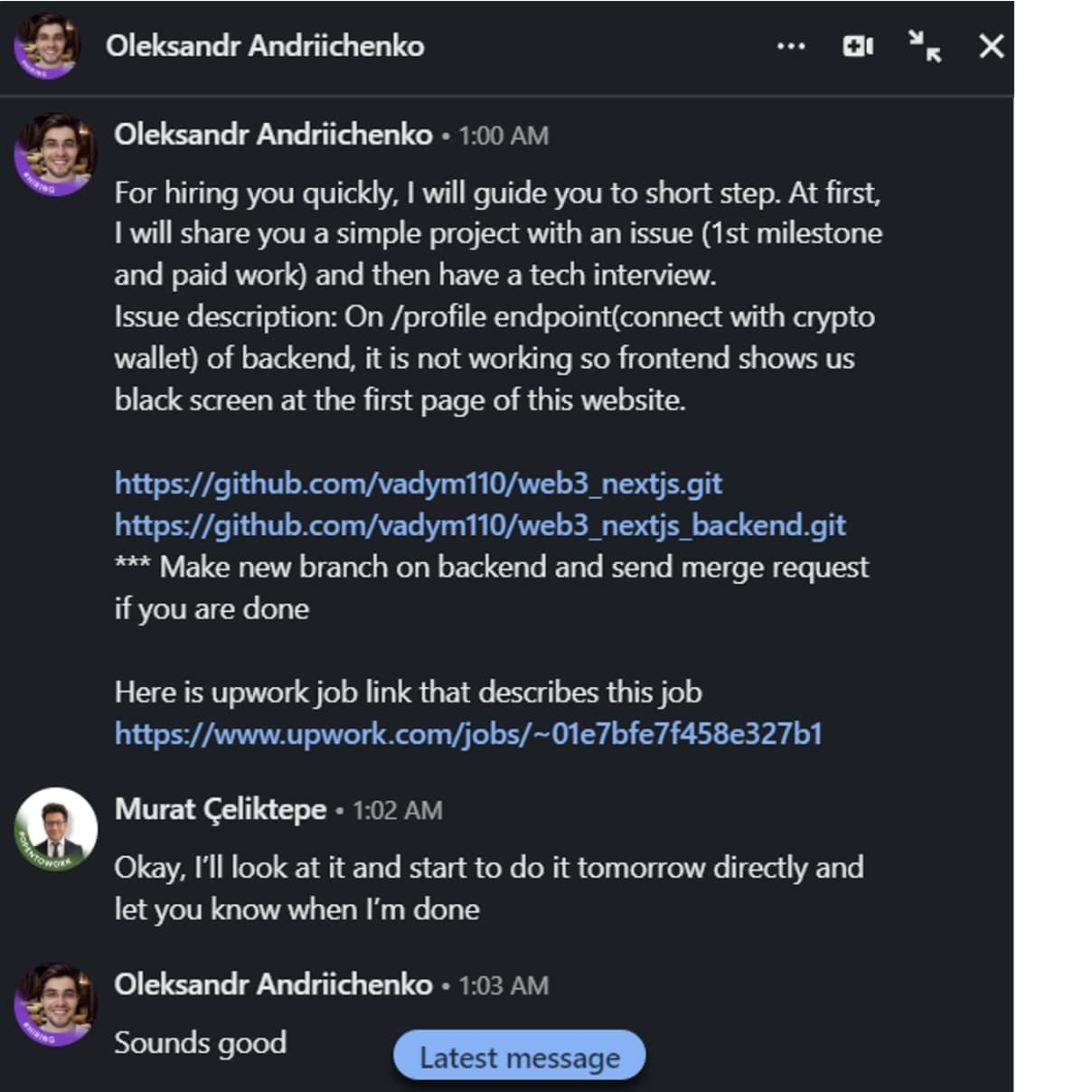
Community Response and Proposed Theories
The developer’s appeal for help attracted both genuine community members and opportunistic crypto bots offering support. Some community insights suggested the npm projects executed by Çeliktepe may have enabled the attacker to deploy a reverse shell, opening up potential vulnerabilities on the developer’s machine.
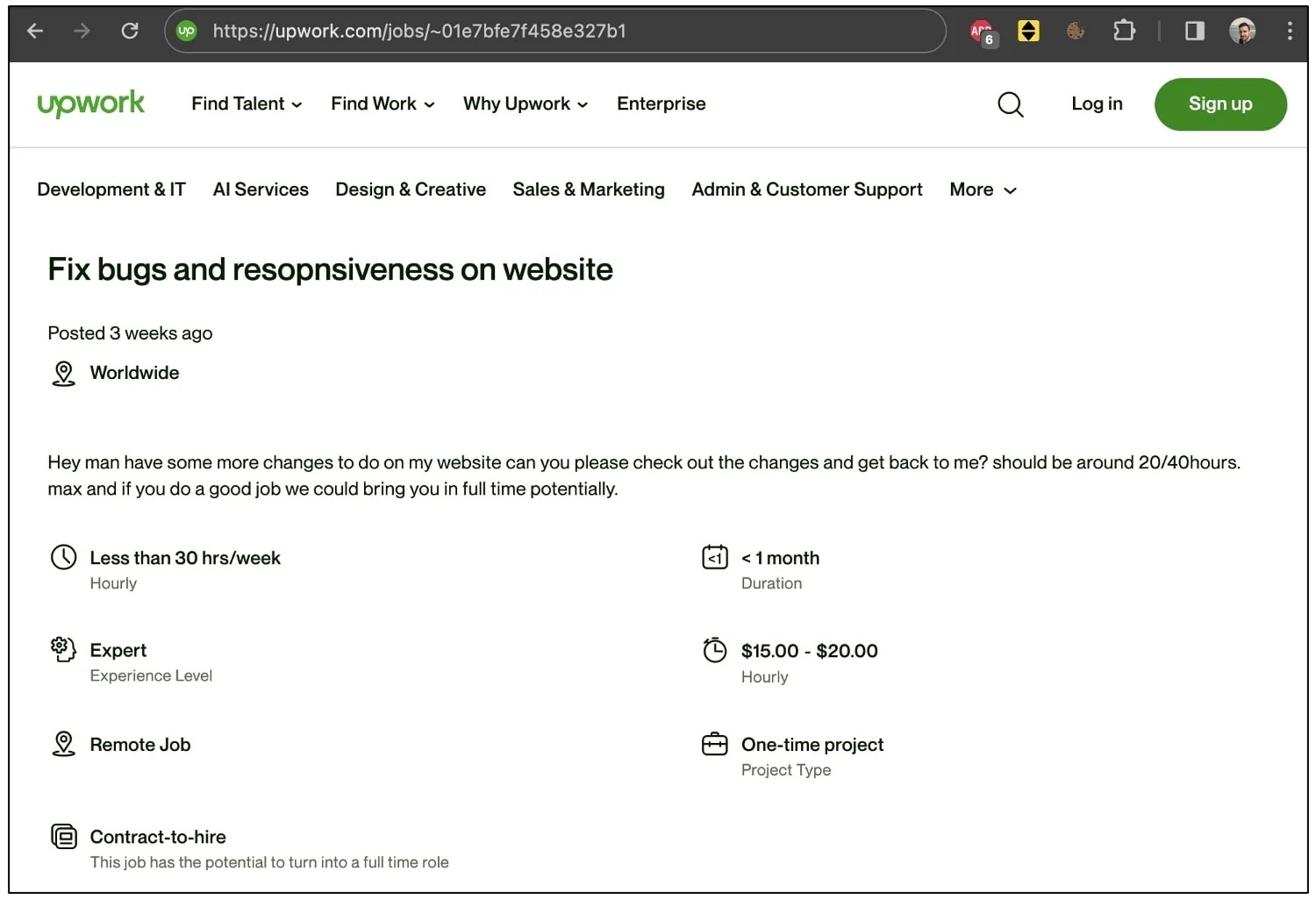
Widespread Targeting by the Same “Recruiter”
Notably, Çeliktepe is not alone in falling prey to this scheme. Other developers, including security researcher Bartu Bozkurt and Mehmet Selim, reported similar LinkedIn approaches from the same “recruiter.” Bozkurt labeled it a “very well-known type of hack,” indicating a systematic and targeted effort to exploit unsuspecting web developers and security researchers.
Caution for the Community
The incident serves as a stark reminder for web developers and security researchers to remain vigilant against fraudulent job offers on professional platforms. Completing any take-home job exercises on a separate (virtual) machine, detached from the primary device, is recommended as a precautionary measure to safeguard against potential scams. As the community grapples with understanding the intricacies of this elaborate attack, collective awareness and caution become crucial to thwart such malicious schemes.