In an official blog post, Crypto exchange Gate.io has announced that the web analytics tool StatCounter has been removed from its website after a breach was reported by Internet security company ESET.
In an official blog post, Crypto exchange Gate.io has announced that the web analytics tool StatCounter has been removed from its website after a breach was reported by Internet security company ESET.
Gate.io said the StatCounter traffic statistics service was removed immediately after ESET received a security alert about suspicious behaviour.
Gate.io said it scanned the site with 56 antivirus products and “no one reported any suspicious behavior at that time.” However, the company changed its traffic tracker and reported that “users’ funds are safe.”
On 6th November the Slovak-based IT security company ESET published a security report claiming that hackers had violated the important web analysis tool StatCounter to target the Bitcoin Exchange (BTC) using the traffic analysis service.
According to ESET researcher Matthieu Faou, the attackers compromised the StatCounter platform, which is evidently utilized by over two million other websites by modifying the JavaScript (JS) code on every page of the website.
The hackers managed to add a malicious code containing “myaccount/withdraw/BTC,” which is intended to replace the destination address of a Bitcoin transfer by Crypto- Exchange users with an address owned by the attackers.
According to Faou, who is allegedly the initial person to identify the “supply-chain attack,” this Uniform Resource Identifier (URI) “myaccount/withdraw/BTC” has been exclusively valid on crypto trade Gate.io, supposedly “the primary target of this attack.”
Currently positioned as the 38th best crypto exchanging platform by the daily trading volume at the time of composing this article, the exchange is very prevalent in China with a rank of 9,382 within the field of domestic traffic, whereas the worldwide rank is 33,365, according to SimilarWeb activity information and analysis tool.
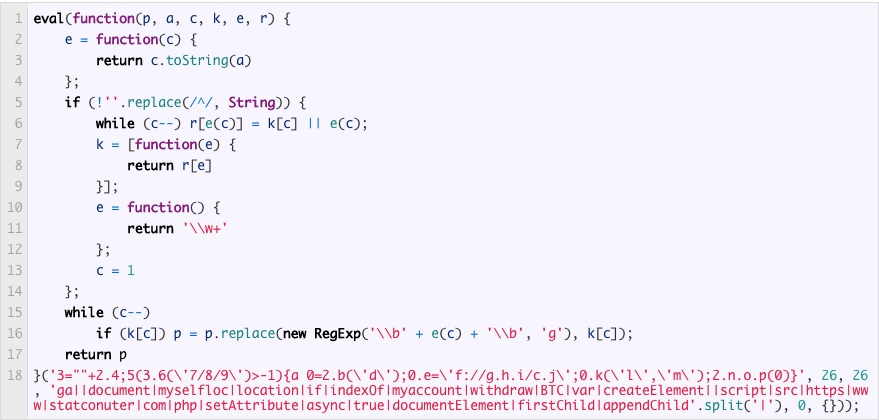
In the conclusion of his report, the ESET researcher stated that the recent breach of security provides further evidence that external “JavaScript code is under the control of a third party and can be modified at any time without notice.”
JS is often one of the most common tools utilized by programmers to execute cryptojacking. According to the investigation, JS-based browser add-ons and extensions are greatly defenseless to programmer assaults and are frequently utilized for covered up mining by utilizing client’s computer assets.
For example, analysts found a crypto-mining malware in mid – October that covers up behind a fake Adobe Flash upgrade.